MIAMI, Nov. 16, 2021 / PRNewswire / – Unified Technologies, a cloud service provider known for its unique integration system for Cyber Security, announced today that the company has successfully completed its System and Team Management System ( SOC). ) 2 Type 2 check and test both cybersecurity and managed IT services.
The SOC 2 report is designed to assure potential and potential customers that the best-of-breed security tools of the type and advanced intelligence (AI) industry are being implemented with expertise by Unified Technologies with advanced features. quality and control methods to process customer data.
“We are pleased that our SOC 2 Type 2 report shows Unified Technologies addresses the risks facing technology service organizations and demonstrates a commitment to protecting our customers’ data,” said Serafin Achurra, Sr. . EVP and CIO at Unified Technologies.
The study, conducted by Kaufman Rossin, the 100th largest CPA company, concludes that Unified Technologies adheres to basic management principles for cloud computing services. Strong Type 2 ratings include values and documentation of events and projects built over the past year.
Determined by the Association of International Certified Professional Investigators (AICPA), SOC 2 Type 2 reports Examining service organizations’ systems, design suitability, and performance and impact control.
Kaufman Rossin’s study concludes that Unified Technologies ’IT management and security services maintain the highest level of security and service efficiency, essential for companies successfully navigating today’s cloud computing environment.
President and CEO of Unified Technologies Tony Silva commended his team of experts and leading partners with the world’s leading technology companies, including Unified Technologies Certification as Microsoft Gold Partner, for the company’s success and prestige very much. In addition, Unified Technologies sheds light on the ‘collaborative management approach’ as a key component.
“At Unified Technologies we know that an efficient, scalable and secure environment is the most important part of any web-based network. if we have our world-class experts who work shoulder-to-shoulder as an upgrade to our client security team, which is confirmed by this SOC2 test, ”said Silva. “Our ability to fill vacancies and customize solutions and equipment with the help of highly skilled and highly skilled technicians delivered can enhance and enhance the capabilities of our customers to ensure their environment and make this cost-effective. very much. “
With personal concerns at all times, the threat of cyber attacks, ransomware, and meteoric attacks in remote business, control and security services provided by companies like Unified Technologies with the certification of SOC 2 is now being censored by experts akari and their importance. longevity.
“At Unified Technologies, we realize that it is not enough to prepare for today. With tools that go beyond the needs of today and with talented technicians who are proud and expect the unexpected, we can deliver to our partners our business is a hardware-based product. and partners that we can rely on, “said Charl Myburgh, Unified Technologies CFO and Senior VP.
TECHNICAL COMPETITIONS A team of highly-skilled, highly-skilled, highly-skilled, highly-skilled, highly-skilled professionals, have an unparalleled level of dedication and expertise in providing reliable, collaborative communication systems. The Unified team consists of world-renowned & amp; expert technical experts and trusted consultants who leverage the best solutions from industry leaders including Cisco, Microsoft, Amazon AWS, HPE, Palo Alto, Fortinet, Netsurion, VMware, Clean Clean, Rubrik, VEEAM, Citrix , Dell Technologies, Darktrace, Datadog, Checkpoint, and ExaGrid. These great partnerships enable our global expertise to deliver the best in class IT and Internet security solutions tailored to meet specific business needs.
Integrated Technology, IT Solutions and Service Provider, always provides protection for customers’ competition by delivering the most reliable, reliable, and flexible IT products. Expertise in vertical markets including Financial Services, Professional Services, Healthcare, Visitors, and Government, Customer Relationships can rely on world class expertise and commitment to customer satisfaction.
SOC 2 TYPE 2 & amp; AICPA Developed by AICPA, SOC 2 Type 2 reports the details of the service organization structure and the appropriateness of design and quality control. The SOC report includes team monitoring, brokerage management, internal management, risk management, regulation, operational reliability, and privacy. The SOC 2 report is unique to each company and includes unique controls for each team, ensuring compliance with trust standards.
Contact: James Goll7866616954 323931@email4pr.com
View original content to download multimedia: https: //www.prnewswire.com/news-releases/unified-technologies-a-leading-managed-services-and-cloud-based-services-company-secures-soc-2- type -service -service-and-protection-for-2-year-2-row-301425576.html
Why is Fortinet so good?
[Fortinet FortiGate] is [another] platform and ready platform for any large organization. Improved network security tools enhance network performance and help you to secure your team from any cyber attack. On the same subject : Top Reasons Why Offering Managed MDM Services Accelerates MSPs’ Growth. This is also a great selling point due to the advanced features of security, speed control and low cost.
Why is FortiGate the best?
Why should I use Fortinet?
The primary reason the partners chose Fortinet was for its reputation as a major cybersecurity company, including security solutions for network, end-to-end, applications, data center and cloud – with tools designed to make acting as a coalition. See the article : Evolution of managed services.
What is the use of Fortinet?
Fortinet provides advanced network security solutions that protect your network, users, and data from further threats. Extending our portfolio of high-value and centralized management systems allows to strengthen security and provide easy, end-to-end security tools.
How good is Fortinet?
“Review for Fortinet Firewall” It has the best security features compared to others and excels in the game as well. We implement FG Firewalls in many of our databases and still deliver the best results. It is very easy to set up, set security rules, access.
How good is Fortinet?
“Review for Fortinet Firewall” It has the best security features compared to others and excels in the game as well. We implement FG Firewalls in many of our databases and still deliver the best results. See the article : Aunalytics Unveils Secure Managed Services with Integrated Security. It is very easy to set up, set security rules, access.
What does Fortinet do well?
Fortinet now offers an advanced security system that covers everything from traditional office-based security to cloud software that protects employees remotely and securely connected devices.
Are Fortinet firewalls any good?
Fortinet’s FortiGate Firewalls offer strong security at a reasonable price, making them one of the most popular firewall vendors and the most recent occupant of the corporate list. Gartner has appointed one of the three leaders in the Business Network Firewall Magic Quadrant, along with Palo Alto and Check Point.
Why is Fortinet the best firewall?
FortiGate Advanced Filter provides high performance, high security and deep vision for end-to-end protection in a business network. Its built-in security kits (SPUs) offer high performance and low latency.
Which firewall is best and why?
- Bitdefender Total Security. Total security with Firewall protection. …
- Avast Premium Security. Powerful and advanced device filter. …
- Norton 360 Premium. Wall protection with many features and extras. …
- Panda Dome Important. A good value firewall and internet security solution. …
- Webroot AntiVirus. …
- Regional Mark. …
- GlassWire. …
- Comodo Firewall.
Why do we need Fortinet firewall?
FortiGate Firewalls are built with security controllers to allow industry-wide protection and functionality for encrypted SSL traffic. By providing a vision of applications, users, and IOT devices, these devices are designed to identify topics quickly and comprehensively.
What are the 2 main types of firewall?
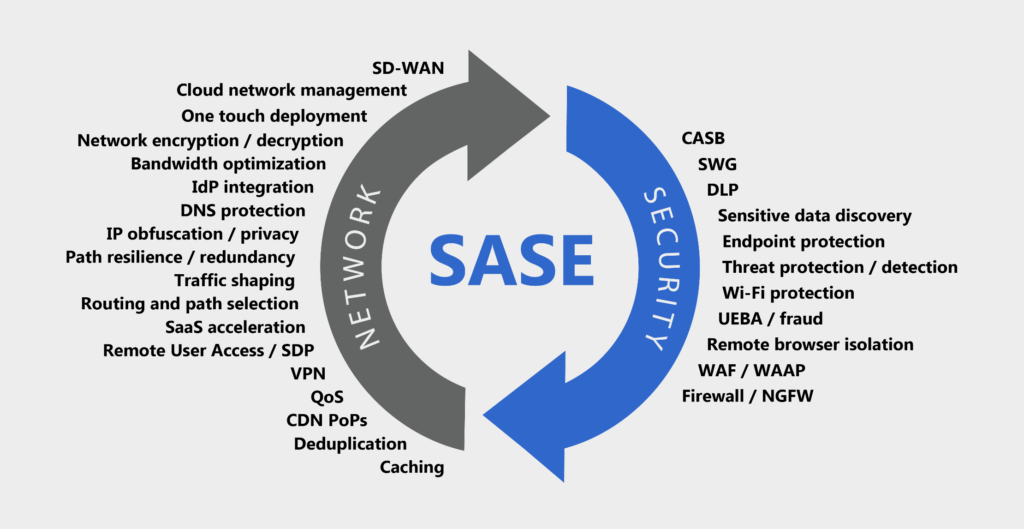
This post reviews the first two types of wallpapers – vehicle search engines and interactive search engines. Types of filtering technology currently on the market: packet filtering, navigation-level navigation, state viewing, application level gateway, multitasking, and UTM.
Can you get 2 Firewalls? Never turn on two lights together because they may collide with each other, and cause system errors that will never occur if you run one of the different filters. We recommend that you not only disable, but also completely remove, the rest of the fire towels you had during the CPF process.
What are the main types of firewall?
5 different types of fire are described
- packet filter Filter
- Navigation level door.
- Application level gateway (aka proxy Firewall)
- State inspection filter
- Next Generation Filter (NGFW)
What are the four basic types of firewall rules?
Four basic types of filter protection exist – network level, circle level, application level and state multilayer.
How many types of firewalls are used?
Four Types of Fire. Firewalls are also distributed based on their performance, and each type can be configured either as a software or as a physical device. Depending on their design, there are four different types of towels.
What are the two main types of firewall quizlet?
What are the two types of Firewall? and Firewall software.
What are firewalls quizlet?
What is a Firewall? hardware or software system that prevents access to or from an unauthorized network. – is used to share a secure network from an unsafe network. – Actually works like a filter and stops unsafe network or packet traffic. It protects the network from external attacks.
What are the two basic functions of a firewall?
A fire extinguisher is a measure of protection that protects a person’s or a company’s computer network. It provides two basic security functions, including packet filtering, which monitors traffic at the packet level, and acts as an application proxy, providing security measures at the application level.
What are the two purposes of the firewall?
They can protect devices from malware, Layer-app attacks and provide information about assets at risk. Firewalls are often used to protect local networks from threats to external networks such as the Internet.
What are the two main parts of a firewall?
Generally, there are two types of towels; Network Firewall is a software application that runs on hardware that filters traffic between two or more networks, while a host firewall is a software layer on a single environment that filters traffic within a computer one.
Why do we need Fortinet firewall?
FortiGate Firewalls are built with security controllers to allow industry-wide protection and functionality for encrypted SSL traffic. By providing a vision of applications, users, and IOT devices, these devices are designed to identify topics quickly and comprehensively.
Why do we need Firewalls? Firewalls provide protection from cyber attackers by protecting your computer or network from malicious or useless network traffic. Firewalls can also prevent malicious software from entering a computer or network.
Why should I use Fortinet?
The primary reason the partners chose Fortinet was for its reputation as a major cybersecurity company, including security solutions for network, end-to-end, applications, data center and cloud – with tools designed to make acting as a coalition.
Why is Fortinet the best firewall?
FortiGate Advanced Filter provides high performance, high security and deep vision for end-to-end protection in a business network. Its built-in security kits (SPUs) offer high performance and low latency.
How good is Fortinet?
“Review for Fortinet Firewall” It has the best security features compared to others and excels in the game as well. We implement FG Firewalls in many of our databases and still deliver the best results. It is very easy to set up, set security rules, access.
Why is Fortinet the best firewall?
FortiGate Advanced Filter provides high performance, high security and deep vision for end-to-end protection in a business network. Its built-in security kits (SPUs) offer high performance and low latency.
Which firewall is best and why?
- Bitdefender Total Security. Total security with Firewall protection. …
- Avast Premium Security. Powerful and advanced device filter. …
- Norton 360 Premium. Wall protection with many features and extras. …
- Panda Dome Important. A good value firewall and internet security solution. …
- Webroot AntiVirus. …
- Regional Mark. …
- GlassWire. …
- Comodo Firewall.
How good is Fortinet?
“Review for Fortinet Firewall” It has the best security features compared to others and excels in the game as well. We implement FG Firewalls in many of our databases and still deliver the best results. It is very easy to set up, set security rules, access.
What are different types of firewalls?

The most common types of standard firewall operating systems are:
- Filter Filter Packet
- Proxy Firewalls.
- NAT Firewalls.
- Web application filtering.
- Next Generation Filter (NGFW)
What are the 3 types of fire? There are three basic types of firearms that companies use to protect their data & devices to protect damaged objects from the network, viz. Packet Filter, State Inspection and Fire Service of Agent Server. Let us give you a brief overview of each of these.
What is stateful and stateless firewall?
Ground walls are designed to protect networks based on information such as location and destination. Given that firefighters filter the packet in the context of a complete internet connection, state-of-the-art fire filters filter the packet on each individual packet.
What is the difference between a stateless firewall and a stateful one?
Given that firefighters filter the packet in the context of a complete internet connection, state-of-the-art fire filters filter the packet on each individual packet. To do this, state fire filter uses packet filter rules that specify specific game conditions.
What is stateful firewall?
State filter is a type of firewall that maintains traffic and monitors active internet connection while analyzing incoming traffic and looking for potential traffic and data risk.
How does Fortinet firewall work?
In short, FortiGate filtering works by analyzing the data entering your network and verifying whether it is safe to transfer to your business. Small specific fire towels will check this information by data such as location and source.
Is the fortinet a good wall of fire? Fortinet Network Firewalls protect each side on any scale with Security-Enhanced Communications. The Secure Network Security network enhances network connectivity and security to protect any side, including business data center, WAN, and cloud edges â â “all from a single network filtering platform.
How does FortiGate firewall give Internet access?
How does FortiGate firewall work?
How Does the FortiGate Firewall Work? In short, FortiGate filtering works by analyzing the data entering your network and verifying whether it is safe to transfer to your business. Small specific fire towels will check this information by data such as location and source.
How firewall works step by step?
When Filter Filter uses a packet filter, the packet that is trying to enter the network is run by a group of filters. These filters remove packages that are relevant to certain specific threats identified and allow others to reach their intended destination. Agent Service.
How does a firewall work PDF?
The WiFi controller takes over all the wireless connections and connects them to multiple channel keys. Multiple port keys are connected to a network router / filter. This connection is displayed as a solid orange line between multiple port keys and network router / filter.
How do firewall devices work?
The most basic types of Firewall software use pre-designed security rules to create filters â € idan if the incoming data pack (small pieces) filters are marked, it is not allowed. The package that does it is sent by filtering to the request system and all others are discarded.
Why is Fortinet the best firewall?
FortiGate Advanced Filter provides high performance, high security and deep vision for end-to-end protection in a business network. Its built-in security kits (SPUs) offer high performance and low latency.
How good is Fortinet?
“Review for Fortinet Firewall” It has the best security features compared to others and excels in the game as well. We implement FG Firewalls in many of our databases and still deliver the best results. It is very easy to set up, set security rules, access.