MCLEAN, Virginia and BEDFORD, Mass., Oct.20, 2021 / PRNewswire / – MITER Engenuity ™ today announced its first invitation to participate in ATT & amp; CK® assessments for managed services specifically designed for managed security service providers ( MSSP) and Managed Detection and Response (MDR) skills. The goal of this new offering is to provide transparency in the capabilities of the MSSP and MDR. The first invitation to participate in ATT & CK Managed Service Assessments is open until December 29, 2021.
So far, MITER Engenuity ATT & amp; CK Evaluations has focused on evaluating the potential ability of products to detect and protect against known adversary behaviors. “This has helped lift the entire endpoint security market through transparency for end users and collaboration with capacity providers,” said Holger Schulze, CEO and editor of Cybersecurity Insiders, an infosec industry inspector. By extending ATT & CK assessments to evaluate managed services, MITER Engenuity will help increase community trust in their suppliers and help advance the services and skills they offer.
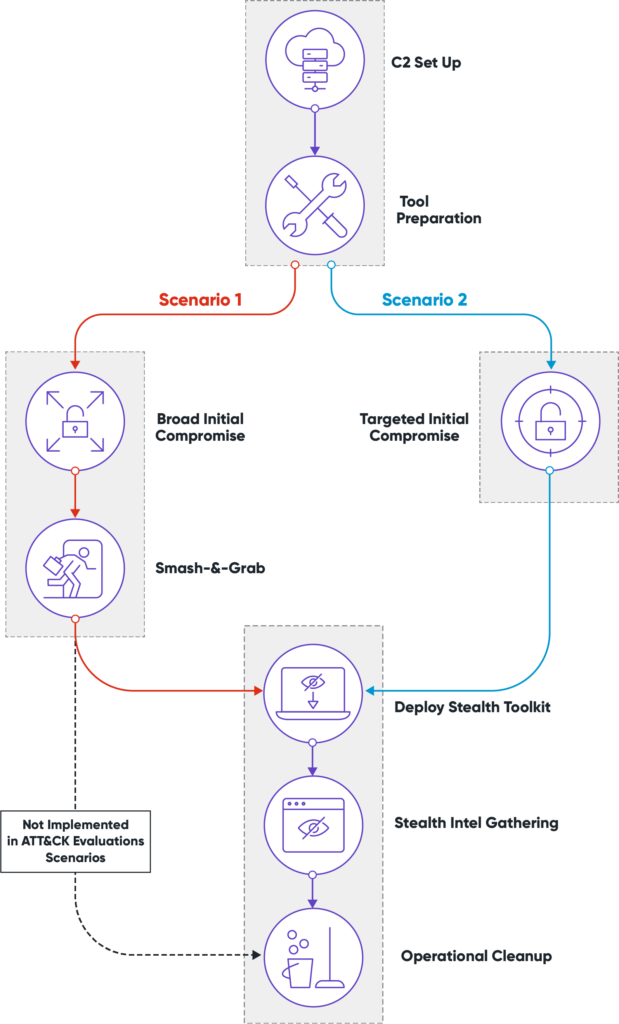
Designed to focus on the people managing the security technology, versus the effectiveness of vendor products per se, ATT & CK Managed Services assessments will not reveal the emulated adversary prior to assessment. This is a significant change from the open book format used in Enterprise ATT & CK assessments which seeks to remove the human element from the technology assessment. Participants will reconstruct behavior as if a normal user had been hacked, truly testing skills in a threat-aware scenario. The results will be made public after the completion of the evaluations.
“We are extremely excited to extend ATT & CK evaluations to the managed services industry, highlighted by the MSSP and MDR capabilities,” said Frank Duff, general manager of ATT & CK Evaluations. “Based on our business assessments, this evolution of the ATT & CK Evaluations program will enable us to evaluate and improve services that leverage these technologies to secure networks.”
The need for these new assessments is underlined by the preliminary results of the “Report on Managed Services 2021: No Rest for the Wary” conducted by Cybersecurity Insiders. The report found that the community has a high dependency on services, but wavering confidence in the security that managed detection and response (MDR) and managed service security providers (MSSPs) offer businesses. The survey to date reveals that:
This assessment will provide MSSP and MDR capability providers the opportunity to demonstrate their ability to identify threats within an organization. This will also benefit potential customers of these features as the end user will gain a clearer understanding of how threats are addressed, all while capacity providers will learn their strengths and weaknesses to validate and improve their own. post-exploit analysis capabilities.
The ATT & CK Managed Services Assessments will take place in Q2 2022 with results expected for Q3 2022. For a complete overview and to learn more about our assessment process, or contact the ATT & CK Assessment Team , please visit https://attackevals.mitre-engenuity.org.
About MITER EngenuityMITER Engenuity is a technology foundation that works with the private sector on challenges that require public interest solutions, to include cybersecurity, infrastructure resilience, health effectiveness, microelectronics, quantum sensing and next-generation communications. www.mitre-engenuity.org.
How many tactics does Mitre ATT&CK have?
The latest version (version 9) of the Enterprise ATT & CK matrix includes 14 tactics listed in a logical sequence, indicating the possible stages of an attack. See the article : United States and Puerto Rico IT Managed Services Market to.
Is Miter ATT & amp; ck a threat model? MITER ATT & CK Framework MITER ATT & CK is designed to support cybersecurity by providing a framework for threat modeling, penetration testing, defense development, and similar cybersecurity exercises. … The combination of tactics and techniques provides concrete guidance for a threat modeling exercise.
What is Mitre ATT&CK and how is it useful?
ATT & CK can be useful for cyber threat intelligence as it allows you to describe contradictory behaviors in a standard way. To see also : IDC Survey Shows That Managed Service Providers Face Numerous Challenges in the Evolving and Highly Competitive Managed Cloud Services Market. … Creating MITER ATT & CK Navigator voices for specific actors is a good way to visualize the strengths and weaknesses of the environment compared to those actors or groups.
What is the purpose of the Mitre?
A Definition of the MITER ATT & CK Framework The MITER ATT & CKâ „framework is a comprehensive array of tactics and techniques used by threat hunters, Red Teams, and defenders to better classify attacks and assess an organization’s risk.
What is Mitre ATT&CK evaluation?
Leveraging the knowledge base of MITER ATT & CK®, the assessments evaluate various vendors on their ability to automatically detect and respond to cyber attacks in real life within the context of the ATT & CK framework.
What are Mitre ATT&CK tactics?
MITER ATT & CK® stands for MITER Adversarial Tactics, Techniques and Common Knowledge (ATT & CK). The MITER ATT & CK framework is a curated knowledge base and model for cyber adversary behavior, reflecting the various stages of an adversary’s attack life cycle and the platforms it is known to target. This may interest you : Ntiva Announces Acquisition of Managed Services Provider Navakai.
How many techniques are in MITRE ATT&CK?
The ATT & CK Enterprise matrix is a superset of the Windows, MacOS and Linux matrices. As of this writing, there are 245 techniques in the Enterprise model. MITER regularly updates ATT & CK with the latest and greatest hacking techniques that hackers and security researchers discover in the wild.
What is MITRE testing?
The MITER Round 1 assessment was essentially a product assessment focused on measuring the detection capabilities of the EDR in a controlled environment with the main assessment criteria being telemetry and detections.
How many tactics does Mitre ATT&CK have?
The latest version (version 9) of the Enterprise ATT & CK matrix includes 14 tactics listed in a logical sequence, indicating the possible stages of an attack.
Is nobelium a cozy bear?

The group has been given various nicknames by other cybersecurity companies, including CozyCar, CozyDuke (from F-Secure), Dark Halo, The Dukes (from Volexity), NOBELIUM, Office Monkeys, StellarParticle, UNC2452, and YTTRIUM. …
What is APT3? APT3 is a China-based threat group that researchers have attributed to the Chinese State Security Ministry. This group is responsible for the campaigns known as Operation Clandestine Fox, Operation Clandestine Wolf, and Operation Double Tap.
What are apt groups?
An advanced persistent threat (APT) is a stealth threat actor, typically a national state or state-sponsored group, that gains unauthorized access to a computer network and remains undetected for an extended period.
What does APT group mean?
Advanced Persistent Threat (APT) groups are broadly classified as organizations that conduct “attacks on the information assets of a country of national security or strategic economic importance through cyber espionage or cyber sabotage.” They are elusive, eminent and effective at what they do: wreaking havoc on their …
What is an example of APT?
APTs are generally sponsored by very large nations or organizations. Examples of APTs include Stuxnet, which brought down Iran’s nuclear program, and Hydraq. In 2010, US and Israeli cyber forces attacked Iran’s nuclear program to slow the country’s ability to enrich uranium.
What is UNC2452?
UNC2452: A highly evasive attacker exploits the supply chain to compromise objectives. Updates for customers and a broader cybersecurity community on how to take steps to defend against the attacks seen during this global campaign.
How does Sunburst attack work?
SUNBURST is a massive fifth generation cyberattack conducted against US government agencies and technology companies. … SUNBURST is a supply chain attack that targets large organizations indirectly by violating their direct suppliers. Attackers used SUNBURST to hack US software company SolarWinds.
What is a sunburst malware?
Sunburst is a digitally signed component of SolarWinds of the Orion software framework that contains a backdoor that communicates via HTTP with third-party servers. … Sunburst uses multiple obfuscated blocklists to identify running security and antivirus tools such as processes, services, and drivers.
What is APT29 Mitre?
APT29 is a threat group that has been attributed to Russia’s Foreign Intelligence Service (SVR). They have been in operation since at least 2008, often targeting government networks in Europe and NATO member countries, research institutes and think tanks.
What is Mitre ATT&CK evaluation?
Leveraging the knowledge base of MITER ATT & CK®, the assessments evaluate various vendors on their ability to automatically detect and respond to cyber attacks in real life within the context of the ATT & CK framework.
What country is APT29 attributed to?
The Russian APT29, which the US government has associated with the Russian foreign intelligence service, is actively serving malware (WellMess, WellMail) previously used in COVID-19 spying campaigns in the UK, US and Canada.
What types of actors may need to be accounted for in your threat model?

Types of threatening actors
- Cyber terrorists. Cyber terrorists are a modern mutation of a widespread global problem that has plagued most countries for decades. …
- Government sponsored / state sponsored actors. …
- Organized Crime / Cybercriminals. …
- Hacktivists. …
- Insiders. …
- Screenplay children. …
- Internal user errors.
Which actors does a threat involve? A threat actor, also called an attacker or bad actor, is an entity that is partially or totally responsible for an incident that has an impact, or could have an impact, on the security of an organization. In threat intelligence, actors are generally classified as external, internal, or partners.
What are threat actor types?
Figure 1: Cyber Threat Actors Hacktivists are often ideologically motivated. Terrorist groups are often motivated by ideological violence. Thrill seekers are often motivated by satisfaction. Insider threat actors are often motivated by discontent.
What are three types of threat agents?
Examples of threat agents are malicious hackers, organized crime, insiders (including system administrators and developers), terrorists, and nation states. [a] individual, group, organization or government that conducts or intends to conduct harmful activities.
What are considered threat actors?
Cyber threat actors are groups or individuals who, with malicious intent, aim to exploit vulnerabilities, low cybersecurity awareness or technological developments to gain unauthorized access to information systems in order to access or otherwise affect victims’ data, devices, systems and networks …
What is a hacktivist group?

Hacktivism is an act of a social or political activist that is carried out by breaking in and wreaking havoc on a secure computer system. Hacktivism is a mix of “hacking” and “activism” and is said to have been coined by the hacktivist group Cult of the Dead Cow.
What is the typical motivation of a hacktivist? What motivates hacktivists? Cyber activists usually have altruistic or ideological motives, such as social justice or freedom of speech. Their goal is to stop services and draw attention to a political or social cause.
What do hacker groups do?
They are a decentralized hacking group known primarily for DDoS cyberattacks. These attacks are often launched against political figures, foreign governments and religious groups. Anonymous’s targets are often groups they regard as corrupt, such as child pornography sites or the Westboro Baptist Church.
Who is the No 1 hacker in world?
Kevin Mitnick, the world’s most famous hacker, will use live demonstrations to illustrate how cybercriminals take advantage of your employees’ trust through the art of social engineering.
What is the difference between hackers and hacktivists?
is that hacking is (computer) the playful solution of technical work that requires a deep understanding, especially of a computer system, while hacktivism is (internet) the practice of promoting a political agenda through hacking, in particular defacendo]] or [[disable | disabling websites].
What is the difference between hacktivists and black hat hackers?
Hacktivism does not fit perfectly into either the categories of white hats or those of black hats. Unlike their white-hat or black-hat counterparts, cyber activists are motivated by politics and not profit. They find themselves ideologically at odds with many organizations and feel justified in their cyber attacks against them.
Are hacktivists criminals?
Cyber activists are groups of criminals who come together to carry out cyber attacks in support of political causes. Cyber activists typically target entire industries, but sometimes attack specific organizations that they believe are out of line with their political views or practices.
What is an example of a hacktivist?
Persons or groups who practice hacktivism are referred to as hacktivists. The targets of cyber activists include religious organizations, terrorists, drug dealers and pedophiles. An example of hacktivism is a denial of service (DoS) attack that shuts down a system to prevent customer access.
What is a hacktivist in computer terms?
Derived from the combination of the words “Hack” and “Activism”, hacktivism is the act of hacking, or breaking into a computer system, for politically or socially motivated purposes. The individual who commits an act of hacktivism is said to be a hacktivist.
What is the typical motivation of a hacktivist?
Cyber activists can be motivated by political views, cultural / religious beliefs, national pride or terrorist ideology. The most notable example was that of a group called Anonymous. This loosely affiliated group of hackers from around the world joined together to attack organizations they believed to be wrong.
What is TTP in cyber security?

Tactics, Techniques and Procedures (TTP) is a key concept in cybersecurity and threat intelligence. The aim is to identify patterns of behavior that can be used to defend against specific strategies and threat vectors used by malicious actors.
What is the TTP attack? Tactics, techniques and procedures (TTPs) are the behaviors, methods, tools and strategies that hackers and cyber threat actors use to plan and execute cyber attacks on corporate networks.
What is TTP in information technology?
Time-Triggered Protocol (TTP) is an open computer network protocol for control systems. It has been designed as a timed fieldbus for vehicles and industrial applications.
What is the P in TTP?
The meaning of TTP is tactics, techniques and procedures; trailer transfer point. OPSEC environment to include the identification of critical information, the OPSEC threat e. This section is intended to provide a reference list of abbreviations and acronyms that are frequently used in oncology.
What does Cali stand for?
US Army Regulation 530-1 redefined critical information into four broad categories, using the acronym CALI: capabilities, activities, limitations (including vulnerabilities) and intentions.
What does TTP mean in cyber security?
tactics, techniques and procedures (TTP)
What is TTP IOC?
1. The final game: take advantage of the weak attacker. Spot with TTP based detection. Indicators of Compromise (IOCs) are a losing battle for security teams as they can be easily changed by attackers. Adopting a detection strategy based on tactics, techniques and procedures (TTP) restores power to the defender.
What does TTP stand for in security?
Tactics, techniques and procedures (TTPs) are the “patterns of activity or methods associated with a specific threat actor or group of threat actors”. TTP analysis aids in counterespionage and security operations by describing how threat actors carry out attacks.